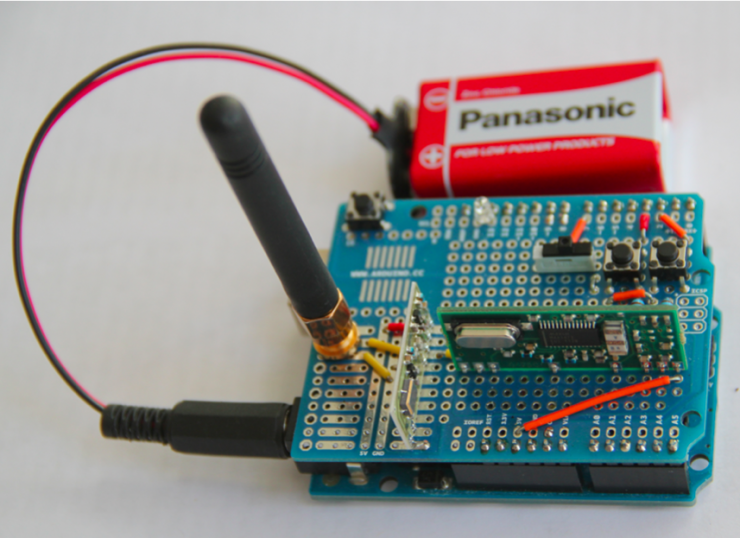
A wave of researchers at the University of Birmingham in the United Kingdom "had" on the Volkswagen Group. Three years ago, they discovered a loophole in Volkswagen's ignition system that was sued by the public and forced to postpone the publication of research results. As a result, this team "has become more and more brave" and this week again revealed a major loophole in Volkswagen's keyless entry system, affecting 100 million cars worldwide, which is embarrassing. In 2013, Flavio Garcia, a computer scientist at the University of Birmingham in the United Kingdom, and his colleagues discovered a major loophole in Volkswagen's starting ignition device. Through this loophole, millions of Volkswagens can be remotely started. You don't need to start the car key, you can open it. But at that time, the research team suffered a lawsuit from the public. The publication of research results and disclosure of vulnerabilities was forced to be postponed for two years and finally announced in 2015. However, this experience did not diminish the spirit of the Garcia team. On the contrary, they carried out more in-depth research on the defects of Volkswagen. Now, they have seized another weakness of Volkswagen: not only is the ignition device flawed, but its keyless entry system also has major loopholes. Moreover, the scope of this loophole is staggering: all Volkswagen cars sold since 1995, that is to say, users of about 100 million Volkswagen cars worldwide are threatened. Flavio Garcia, picture from his personal official homepage Recently, at the Usenix Security Conference in Austin, Texas, USA, Garcia led three other researchers from the University of Birmingham in the United Kingdom to publish a paper entitled "Locked and White Locked--About Car Remote Keyless Entry." "Lock It and Still Lose It - On the (In) Security of Automotive Remote Keyless Entry Systems" gives the public a punch. Interested friends can click here to view the original article. The paper describes two types of keyless entry vulnerabilities. The first one concerns the Volkswagen brand, which affects every vehicle sold by the public for 20 years, including Audi and Skoda. The second is a cryptographic system called "Hitag2" that involves a variety of car brands, including Alfa Romeo, Citroen, Fiat, Ford, Mitsubishi, Nissan, Opel and Peugeot. The attack principle for the two types of vulnerabilities is simple: Use a wireless device to intercept the owner's key signal, and then "clone" the exact same key. At the same time, both attacks do not require expensive equipment. They only need to connect the computer to a device that intercepts signals, or use a more compact "Arduino motherboard + radio receiver" kit. This can be purchased for as little as $40. To. $40 Arduino Unlimited Access Device Garcia said: "Hardware costs are low, the design is simple, and its function is almost the same as the original remote control." In both attacks, vulnerabilities for Volkswagen branded cars are more problematic. This is because, as David Oswald of the University of Birmingham puts it, “You only have to tap the signal once and you can clone the car key and you can drive and lock the car many times.†Volkswagen's keyless entry system includes two kinds of "key value", one is shared by millions of cars, and the other is unique to each car. First, the researchers conducted a "complicated reverse engineering" of a component of the Volkswagen in-vehicle network and extracted the "shared key value." Then, just wait for the owner to press the button of the remote control key, and issue the unique key value of the vehicle. The researcher intercepts this signal through the aforementioned device to obtain the “unique key valueâ€. By combining the two, you can clone the complete key for each car. In order to ensure the success of the "eavesdropping", the wireless bugging device must be within 90 meters of the owner. Also, the attacker must have the correct "shared key value." In the past 20 years, among the 100 million vehicles sold by the public, the most commonly used are only four types of keys. However, there are "exceptions", such as the Golf 7 and the use of a specific key model, to be able to avoid attacks. Fortunately, the researchers did not disclose in public papers which part of the vehicle the “shared secret key†was stored in, so as to prevent intruders from taking the car. In addition, for the Hitag2 cryptosystem, this attack method does not need to extract the "shared key" we mentioned earlier, but also intercepts the 8-bit code sent by the owner key in an eavesdropping manner. The vulnerability in the HiTag2 encryption scheme allows researchers to break a car in one minute. After discovering vulnerabilities, the researchers wrote a letter to the public to inform the existence of the vulnerabilities. On this matter, the public did not give any reply. Joon Knapen, a spokesperson for chip supplier NXP, said: “HiTag2 is an encryption algorithm that we used 18 years ago and it is already very old. Since 2009, we have replaced more advanced encryption algorithms. And we had a few years ago Start suggesting our customers not to use the HT2 encryption algorithm in new projects." However, at the end of the paper, the researchers proposed a temporary solution to the majority of owners: if there are valuable items in the car, it is recommended to stop using the keyless entry system or simply remove the system and use a traditional mechanical lock instead. Via The Wired 76mm Desktop Dot Matrix Printer
Qunsuo is the best supplier Manufacturer of Desktop Dot Matrix printer.
1. Adopt the new technology and material of high quality shell, beautiful appearance, and equipped with a larger capacity of paper bin.
2. Bluetooth, USB and serial port are optional for easy connection.
3. Equipped with paper shortage alarm, overheating protection, HP back, black calibration functions, high intelligence.
4. Equipped with original Epson printing movement for longer service life.
5. Applicable to logistics, traffic police, postal, urban management, tobacco, meter reading, supermarkets, clothing and other industries and fields.
Dot Matrix Printer,Portable Dot Matrix Printer,Bluetooth Dot Matrix Printer,Android Handheld Dot Matrix Printer Shenzhen Qunsuo Technology Co., Ltd , https://www.qsprinter.com