[PConline News] Not long ago, researchers uncovered that Intel's Management Engine (ME), a component found in many of its recent processors, is actually a full-fledged operating system with access to Ring-3 privilege levels—higher than regular user applications. Even when the system is turned off, this mini OS can still run, and Intel has never officially disclosed such details. Experts warn that if exploited, these capabilities could pose a serious security risk. Recently, Intel finally acknowledged the issue by releasing a security advisory detailing up to 11 vulnerabilities within the ME system.

Earlier reports revealed that MINIX, an ultra-light Unix-like operating system, runs inside the processor with its own dedicated CPU core and firmware. It operates independently and remains invisible to users. While standard software runs at Ring-3, and the OS kernel at Ring-0, MINIX has direct access to Ring-3. This means it can operate even when the system is powered down, as the ME is designed to start alongside the processor and manage critical security functions at the hardware level.
With such high-level access, if compromised, an attacker could gain full control over the system—even when it's shut off. This raised significant concerns about the potential for catastrophic security breaches. Many users were alarmed by the implications of such a hidden, powerful subsystem running beneath their operating systems.
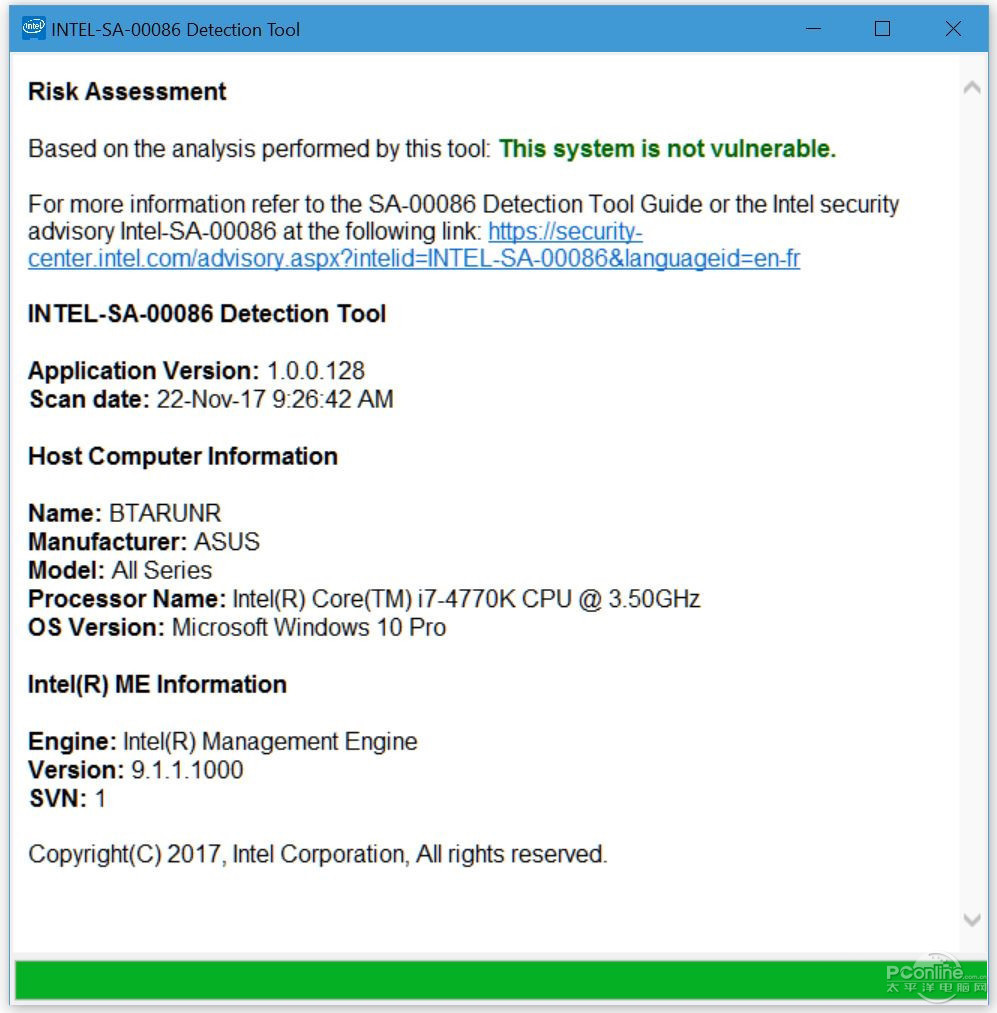
In response, Intel recently published a security bulletin confirming that the ME version 11.0.0–11.7.0, along with Trusted Execution Technology (TXT) 3.0 and Server Platform Security (SPS) 4.0, contains more than 11 vulnerabilities affecting various processor models. These include:
- Sixth-generation Core (Skylake)
- Seventh-generation Core (Kaby Lake)
- Eighth-generation Core (Coffee Lake)
- Xeon E3-1200 v5/v6 series
- Xeon Scalable series
- Xeon W series
- Atom C3000 series
- Apollo Lake Atom E3900 series
- Apollo Lake Pentium and Celeron N/J series
These flaws could allow attackers to inject and execute arbitrary code, leading to system instability, crashes, or even complete compromise. The attacks are undetectable by the OS and users, making traditional software-based defenses ineffective.
This discovery marks a major development in processor-level security. While Intel has released a testing tool for Windows and Linux users, and claims patches are already in development, the full extent of the impact remains unclear. The vulnerability highlights the risks of having hidden, powerful components embedded in modern CPUs.
It’s also unknown whether AMD or other manufacturers have similar issues. As this story continues to unfold, users should stay informed and follow official updates from their hardware providers to ensure their systems remain secure.
Output Transformer,Output Transformers,Pin Plug Switching Power Transformer,Output Switching Power Transformer
Huizhou Show-Grand Electronics Co., Ltd. , https://www.sgtransformer.com